Canon cures security vulnerabilities in all cameras affected by malware risk
Canon firmware 'cures' all 33 cameras affected by major security vulnerability
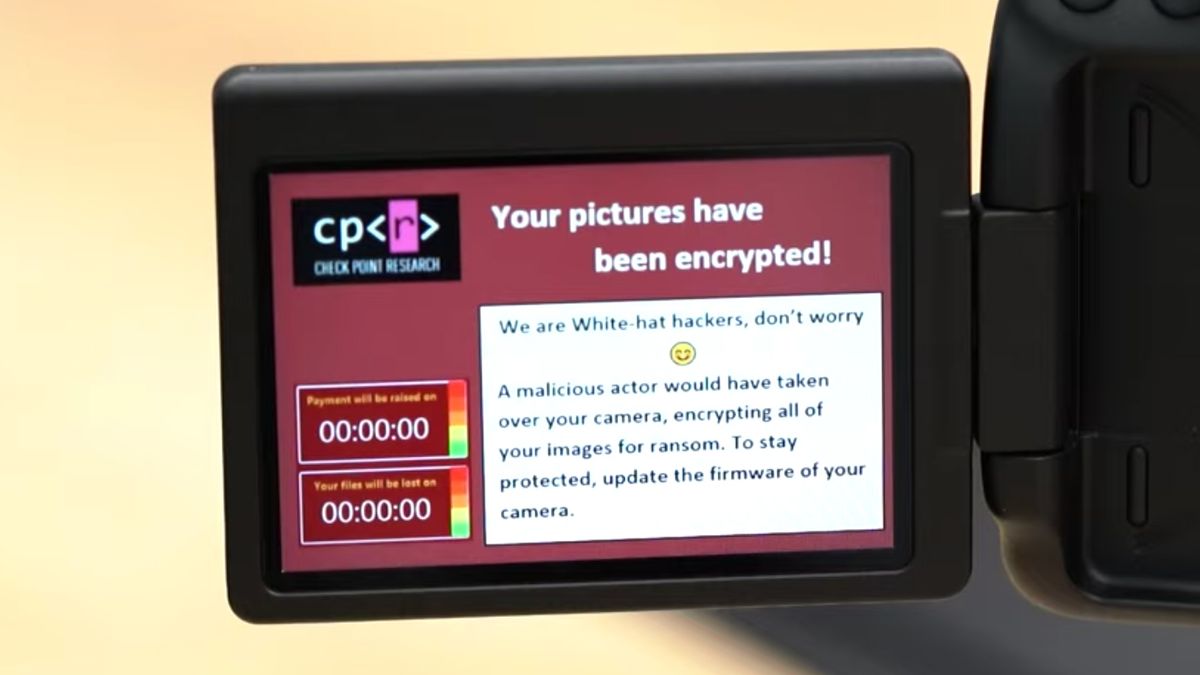
Last August, a serious cybersecurity alert was issued as 30 Canon cameras were found susceptible to critical Wi-Fi and USB vulnerabilities, leaving them open to infection by ransomware – a type of malware whereby cyber-attackers can hold photos and videos taken on the camera to ransom.
By November the number of affected Canon cameras was increased to 33 – and the core issue, a vulnerability in a standard communication protocol, potentially leaves cameras from other manufacturers vulnerable as well. For its part, though, Canon has been proactive in the process and has now released corrective firmware for all its affected cameras.
The vulnerabilities were discovered by cybersecurity firm Check Point Software Technologies, which alerted Canon about the problem affecting its mirrorless, DSLR and compact camera lines. Check Point singled out the Canon EOS 80D, releasing a video demonstrating how easy it is to exploit holes in the standard Picture Transfer Protocol (used to transfer files from cameras to PCs) to infect the camera and computer.
“Any ‘smart’ device, including cameras, are susceptible to attacks,” said Eyal Itkin, Security Researcher at Check Point. “Cameras are no longer just connected via USB, but to WiFi networks and their surrounding environment. This makes them more vulnerable to threats as attackers can inject ransomware into both the camera and PC it is connected to. Hackers could then hold peoples’ precious photos and videos hostage until the user pays a ransom for them to be released.”
Since the Protocol is standard, and embedded in other models from other manufacturers, innumerable non-Canon cameras may also be affected. "We focused on Canon as a test case, as they have the largest market share," we were told by Check Point researcher, Eyal Itkin.
"However, the Picture Transfer Protocol is standardized and supported by all digital cameras, regardless of the vendor. While the Canon EOS 80D was the one tested in this demonstration, we do believe that similar implementation vulnerabilities could be found in other vendors as well, potentially leading to the same critical results in any digital camera."
When we reached out to all the major manufacturers, only Olympus responded, telling us, "We are currently investigating the effects on our products. As soon as we know the details, we will take necessary action in order to ensure that our customers can use our products safely."
Get the Digital Camera World Newsletter
The best camera deals, reviews, product advice, and unmissable photography news, direct to your inbox!
Below is the full list of Canon cameras affected by the vulnerability, along with links to corrective firmware downloads where available. If you own or use any of these models, we strongly advise updating your firmware as soon as possible.
Canon EOS-1D X (Version 1.2.1 available)
Canon EOS-1D X Mark II (Version 1.1.7 available)
Canon EOS-1D C (Version 1.4.2 available)
Canon EOS 5D Mark III (Version 1.3.6 available)
Canon EOS 5D Mark IV (Version 1.2.1 available)
Canon EOS 5DS (Version 1.1.3 available)
Canon EOS 5DS R (Version 1.1.3 available)
Canon EOS 6D (Version 1.1.9 available)
Canon EOS 6D Mark II (Version 1.0.5 available)
Canon EOS 7D Mark II (Version 1.1.3 available)
Canon EOS 70D (Version 1.1.3 available)
Canon EOS 77D / 9000D (Version 1.0.3 is available)
Canon EOS 80D (Version 1.0.3 available)
Canon EOS M10 (Version 1.1.1 available)
Canon EOS M100 (Version 1.0.1 available)
Canon EOS M2 (Version 1.0.4 available)
Canon EOS M3 (Version 1.2.1 available)
Canon EOS M5 (Version 1.0.2 available)
Canon EOS M50 / Kiss M (Version 1.0.3 available)
Canon EOS M6 (Version 1.0.1 available)
Canon EOS M6 Mark II (Version 1.0.1 available)
Canon EOS R (Version 1.6.0 available)
Canon EOS RP (Version 1.4.0 available)
Canon EOS Rebel SL2 / 200D / Kiss X9 (Version 1.0.3 available)
Canon EOS Rebel SL3 / 250D / Kiss X10 (Version 1.0.2 available)
Canon EOS Rebel T6 / 1300D / Kiss X80 (Version 1.1.1 available)
Canon EOS Rebel T6i / 750D / Kiss X8i (Version 1.0.1 available)
Canon EOS Rebel T6s / 760D / 8000D (Version 1.0.1 available)
Canon EOS Rebel T7 / 2000D / Kiss X90 (Version 1.0.1 available)
Canon EOS Rebel T7i / 800D / Kiss X9i (Version 1.0.2 available)
Canon PowerShot G5 X Mark II (Version 1.1.0 available)
Canon PowerShot SX70 HS (Version 1.1.1 available)
Canon PowerShot SX740 HS (Version 1.0.2 available)
In its initial product advisory, Canon was keen to stress that there have been no cases thus far where the vulnerabilities have resulted in malicious activity. "At this point, there have been no confirmed cases of these vulnerabilities being exploited to cause harm, but in order to ensure that our customers can use our products securely, we would like to inform you of the following workarounds for this issue."
Again, we should stress that this is not necessarily a Canon-specific issue, as it is the Picture Transfer Protocol itself (rather than the cameras) that exhibits the security flaw. Photographers should remain vigilant and check for relevant security updates from the manufacturers of their equipment.
Full technical details of the investigation can be found on the Check Point website.
Read more:
Canon EOS R hacked: Magic Lantern “successfully loaded”
Canon EOS R review
Verbatim Fingerprint Secure Hard Drive protects and encrypts your data

James has 22 years experience as a journalist, serving as editor of Digital Camera World for 6 of them. He started working in the photography industry in 2014, product testing and shooting ad campaigns for Olympus, as well as clients like Aston Martin Racing, Elinchrom and L'Oréal. An Olympus / OM System, Canon and Hasselblad shooter, he has a wealth of knowledge on cameras of all makes – and he loves instant cameras, too.
